“There’s no silver bullet solution with cyber security, a layered defense is the only viable defense.”
– James scott
So, what is Defense in Depth?
Defense in Depth, or layered security/defense, is the act of placing multiple security controls within various layers of a computer network to slow down, deter, or discourage attacks on the network by threat actors. This concept is seen in many aspects and is not explicitly a concept used only in Information Security. You can see it in used in many aspects of physical security in your normal day-to-day life.
Let’s look at a bank, as an example. Many banks require customers to not have hats, sunglasses, or other face coverings when they enter the bank as a way to deter people from hiding their identity. Banks sometimes also employ security guards who will stop anyone who looks suspicious, check bags, or ask them to remove hats or sunglasses. This is an additional layer of security. Next, bank tellers typically have silent alarms they can trigger if they are being robbed. This layer of security sends an alarm directly to local law enforcement agencies to respond. Another layer would be locked cash machines and another layer would be the physical safe or deposit boxes that are also locked.
If someone were planning to rob a bank, they would need to find a way to defeat all the security controls that are in place in order to be successful and make it away before they are caught. As you can see, Defense in Depth makes it much harder to be successful in attacking a target than if they only had one layer of defense. So, then this leads us to the next question.
How does Defense in Depth apply to IT networks?
Much in the same way a bank will create layers of security to defend their important assets, an organization should also create layers of security to defend its assets.
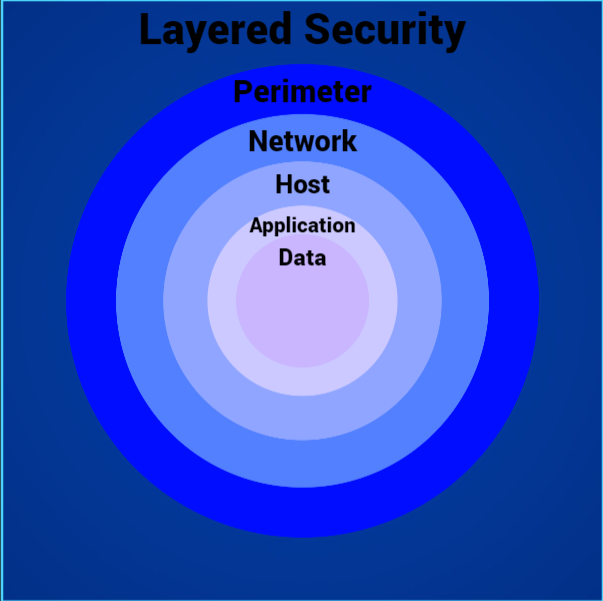
As shown in the simple diagram above, each layer of a computer network should have its own security controls. Let’s explore some examples from these layers:
- Perimeter – Firewalls, Intrusion Detection/Prevention, and Application Gateways
- Network – Web Proxy, Data Loss Prevention, Intrusion Detection/Prevention, Firewalls
- Host – Intrusion Detection/Prevention, Firewalls, Firewalls, Antivirus, Data Loss Prevention, Patch management
- Application – Application penetration testing, Code analysis/code gating, Database monitoring/scanning
- Data – Data Loss Prevention, Data Classification, Encryption, Identity & Access Management
As you can see, there are various ways that an organization can protect its assets and data at every layer of its networks. While the above list isn’t exhaustive, it provides a brief glimpse into what Defense in Depth (or layered security) is.
Bringing it all together
As shown above, using Defense in Depth can significantly increase the overall security posture of any organization. It can also be used for any number of applications outside of InfoSec. In today’s world, attackers are using more sophisticated and high-profile attacks. It is imperative that we, as security practitioners, understand that there is no magic tool, process, or procedure to keep an organization safe. The best way to do this is by working to keep all layers of the organization safe through the use of Defense in Depth.
As you go about your daily life in both your work environment and outside of it, think about all the ways that you see this used in your organization, your bank, your local government offices, or even perhaps even in your own home.
Best of luck to you on your journey!
Further reading:
NIST glossary and links – https://csrc.nist.gov/glossary/term/defense_in_depth
CIS Security Defense in Depth – https://www.cisecurity.org/spotlight/cybersecurity-spotlight-defense-in-depth-did/
SANS White Papers – Defense in Depth by Todd McGuiness 11/1/2001 – https://www.sans.org/white-papers/525/
1 thought on “Defense In Depth – Everything You Need To Know”