Hey guys, back again for another CTF. This time, I’m working through the Offensive Pentesting Path on TryHackMe. I’ve already done several of the boxes, but thought I’d start doing some walkthroughs for other ones on this learning path.
Today, we’re doing the HackPark CTF. The description on this box is that we will brute force a website with Hydra, identify and use an exploit, and then escalate privileges on the windows machine. Pretty straight forward. Let’s get to it!
First off, start up the HackPark machine and either the attackbox or your own VM attack box.
Once everything is up, we’ll start off by scanning the HackPark machine to see what ports and services are available.
Let’s get that nmap scan fired off.

First scan attempt appears to be blocked. This host may not respond to ICMP, so let’s try with a -Pn flag to disable pinging.

There we go. Only seeing 2 ports open. HTTP service on port 80 and Remote Desktop on 3389.
Question 1.
Let’s have a look at that website on port 80 to answer question 1.

There you have it. Pennywise is the clown displayed on the main page. So that answers question 1.
Question 2.
Next, the CTF asks what request type the login form uses on this website. So, let’s do some digging. We first click the hamburger menu in the top right of the website and then click the login link.
Next, let’s review the source code to see what the form uses.
We can do this by either viewing page source or inspecting the site. For this one, I’m doing to inspect the site and then just hover my mouse over the login fields.
However, inspecting shows us this pretty much from the start.
This form uses the post method. That answers question 2.
Question 3.
Next up, the CTF wants us to run hydra on the login form to brute force the site.
Command: hydra -l <username> -P /usr/share/wordlists/<wordlist> <ip> http-post-form
CTF states to guess a username. Well, we shall start off with admin. Because, why not?
However, before we can do this, this command will need some extra things in it before it will work correctly.
This came from some additional research on Hydra and how to use it to brute force http login forms from this site: How to Use Hydra to Crack Passwords: The Complete Guide (stationx.net).
In order to get the rest of the parameters we need, we will need to load up BurpSuite and intercept the login page.
I’m going to try with ‘admin’ and ‘password’ as the credentials.
So, our new command will look like the below:
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.233.116 http-post-form "/Account/login.aspx:__VIEWSTATE=7IqFwhwBIvpdGk0pQ0ZF3BIomgkYkQyGD6UZup8FEEUkYHTnOg%2FAmuqgUJmQP9e1dR6T6ay0%2BJ6abKFmcZyvgYfxrbKCTlNf8Xmgo7wdsV%2BKjdJmjnd%2F4l1nmrLHK0RQP9QMCFJnF1a5L0IGiMtJxkdEZgIxr%2BffwfAIqbMKWOTBSmqQL9YU%2B90MfoJhMHMz0%2Fotm0U9y7FkmbDbkPDOaemscuF0%2FrOmOra5ALVeh5T1EodI4tZtxQd82rdBV86cMTJuONmm%2BWENiz9qdu9FhGNUv0UJ5kP4BB6%2F5%2BeqTy87apAtMu3WPZt%2FaBgNuMld9YbcuWVIQ2jnm%2FWkigmuENKRGzXXv%2FTgRCEwft5rxjnbNAfj&__EVENTVALIDATION=zmoIoariP5yHg8VXF9B4ZfNC%2BAe6y%2Fm3JxdnFBWMFSEFf8R8mjcobRlR7N3nObf7PZCRm27DxhWlkmACyQxF5a575ZZAdyMtLxSoXgz%2FY91iR1JlBEou9MXlVtHCFi%2B5iaGvRUVvOYeC1b1IrlTwcb8WEKLTWnemt5hVlqcwhTgfTnSw&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login Failed"
We must append the path and then the parameters shown at the bottom of the request made when attempting to login as shown above. Remember to replace ‘admin’ and ‘password’ with ^USER^ and ^PASS^, as shown above. Once this is done, we are now ready to launch the brute force attack. (FYI, I used the viewstate parameters from a different request.)
Here’s our results!
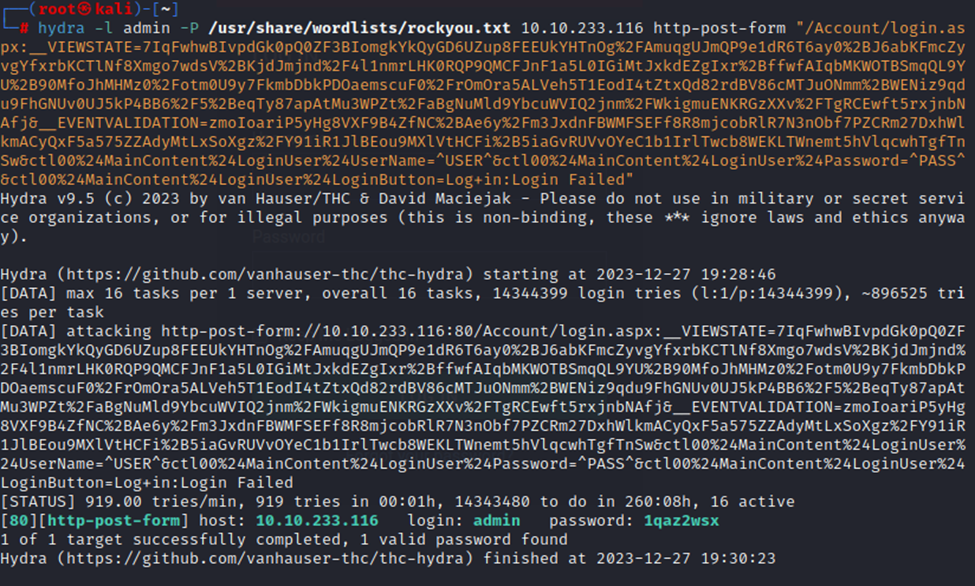
We now have the admin credentials for the site and the answer to question 3.
Question 4.
The CTF now asks us to identify the version of the BlogEngine. Let’s dig around and see if we can find this on the site.
Pretty simple, the about section lists out the version.

That gives us our answer to question 4.
Question 5.
Next the CTF wants us to use the exploit database archive to identify a CVE that will give us a reverse shell for this. http://www.exploit-db.com/ is the site we need to use.
A quick search shows us a potential CVE that is verified and does have an exploit available.

If we click on this and then copy the CVE to our answer, we can confirm that this is the CVE it is looking for.
This answers question 5.
Question 6.
Next the CTF wants us to use this exploit to gain initial access to the server and list what user the web server is running as. So, let’s read the readme details on this exploit.
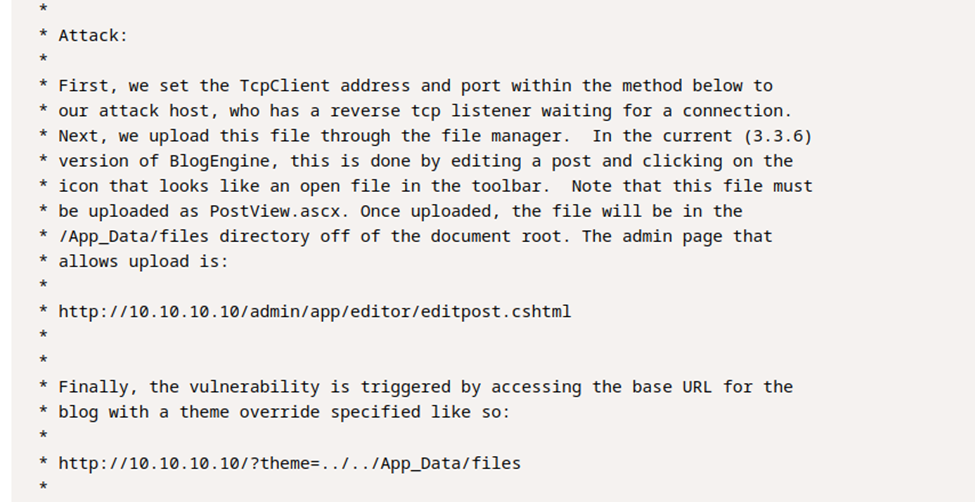
Pretty straightforward. Let’s try it out. So, let’s start by grabbing this script and putting it on our attack box. We will then need to edit it to, as noted in the directions, have our attack box IP and port for a reverse shell connection to reach out to. I suggest downloading the script rather than trying to copy/paste.

Now, with the script edited, we next need to rename it to PostView.ascx. Next, let’s find the upload section and get this uploaded to the blog site.
After browsing the site a little, I noticed that on the ‘Welcome to HackPark’ post, there is a file browser. We should be able to upload our exploit on this post.
Now it is uploaded.
Now, after uploading and saving that post. We need to start our listener. As usual, we’ll use netcat.
Now, we visit the url below to trigger the attack.
http://IP-address-here/?theme=../../App_Data/files
And we have a reverse shell!
Now, lets see who we are to answer question 6.
That answers question 6.
Before we can continue, we will need a more stable shell. Essentially, the shell we have is very finnicky and commands won’t work the best on it. If you try to run something like ‘sysinfo’ on this shell, you may not get any response back from the remote host. This is why we need a stable shell, to ensure that we can continue enumerating and issuing commands on the remote host without issues.
We will use msfvenom to create a reverse shell executable to do this.

We now have an executable that will give us another reverse shell on a different port. Now, serve this up on a web server on my attack box and have the HackPark machine download it. But we must put it in a folder that the current user can probably access. We’ll try the temp folder.
Starting up my web server in my pywww folder where this executable is saved.
Now, on the HackPark shell that we have open, I just need to have it connect and download the executable.
Monitoring my web server, I can see the connection come in and know it was successful.
Now, instead of using a Netcat listener, we will use Metasploit to start a listener before executing our file that we just uploaded.
Load Metasploit with ‘msfconsole’ and then ‘use exploit/multi/handler’. Then, we will set our payload with ‘set PAYLOAD windows/meterpreter/reverse_tcp’. Finally, we set our options. First, check options by just typing ‘options’. We will need to set the LHOST and LPORT to our respective attack box IP and Port that is in the executable we just uploaded.
Your options should now look something like this. Of course, with our own IP and port in place.
Now, simply type run to start the listener.
Finally, we trigger our file. Just go to the C:\Windows\Temp folder and type executable.exe. Replacing ‘executable’ with your file name. This will then trigger the reverse shell that you should see pop up in Metasploit.
(My file didn’t trigger. Why not? Because my machine time ran out. Argh! It takes a while to do the CTF as well as copy/past, edit, and write a walkthrough while I’m doing it.)
After some quick catching back up, we have executed our file and got a shell in Metasploit.

Left side is the victim machine executing our payload and the right is Metsaploit with the new shell.
Question 7.
What is the OS version of the machine?
Now, with our Meterpreter shell, we can run sysinfo and answer question 7.
Meterpreter does have some functions built in such as looking for services. Simply type ‘ps’ in the meterpreter session to see what’s running.
Aside from our, obviously, abnormal jake.exe, I’m seeing something called WScheduler.exe. Looking at the hint, it shows that we should check out the C:\Program Files (x86) directory. Navigating to that in our meterpreter shell, we can see a folder called WindowsScheduler.
Inside this directory we find the WScheduler.exe file. So, this has to be our answer for question 7.
Question 8.
The CTF asks us what binary we should exploit. The hint suggests looking in logs from the abnormal service. In the same folder as the abnormal service and in the running services, I noticed something called Message.exe. The logs in the Events folder also points out this service. Let’s try that for this question.
Bingo!
Message.exe is our answer for question 8.
Question 9.
Next, we need to exploit this and get elevated privileges. This should be fairly simple, since this runs with elevated privileges, we can simply replace this file with a reverse shell, much like we did with msfvenom previously.
Again, moving this into my pywww directory and hosting it on my web server for the HackPark box to grab.
Again, referring to the above, set up Metasploit with ‘use exploit/multi/handler’ and ‘set PAYLOAD windows/meterpreter/reverse_tcp’ and finally setting your options appropriately.
Run it to start the listener.
Finally, let’s download the file from the HackPark box.
In this case, you won’t have to trigger it, because the service gets called frequently. In fact, it started the shell within a few seconds.
Now, we have a higher privilege shell we can use to finish the questions on this box.
And now we have the answer for question 9.
Question 10.
Next, the root flag. This one was pretty simple, just going to the Admin desktop.
The last section talks about escalation without Metasploit. This was a good option as well as it uses WinPeas, one of my favorite tools. In this case, you would want to host the WinPeas.exe file on your attackbox and then using one of the lower privilege shells, download the file and run it on the HackPark box.
I did go ahead and do this, and this was the thing that stuck out quickly to me.
Question 11.
Using Winpeas, what was the original install time?
I didn’t use Winpeas for this, as there’s a simple command to look this up.
systeminfo|find /i "original"
Now, we have our final answer.
Whew!
There was a lot to this one. The usage of msfvenom to create payloads, Metasploit, and using a publicly available exploit for a CVE were all great learning moments on this CTF. Hopefully you learned something from this and can use that new knowledge on further CTF’s in the future. We all run into roadblocks, issues, and sometimes even brick walls when doing these CTF’s, but persistence and drive will get you past those. I appreciate you taking the time to read over this. If you have any questions, corrections, or callouts please feel free to reach out to me!